Vesta Security and Compliance
Last modified: August 12, 2021
Vesta has over 25 years of experience in payments, fraud, and compliance. It is critical to us that we provide best-in-class security and compliance to our partners and their customers. We want to make sure you know we are doing our due diligence based on the Security CIA (Confidentiality, Integrity, and Availability) Triangle.
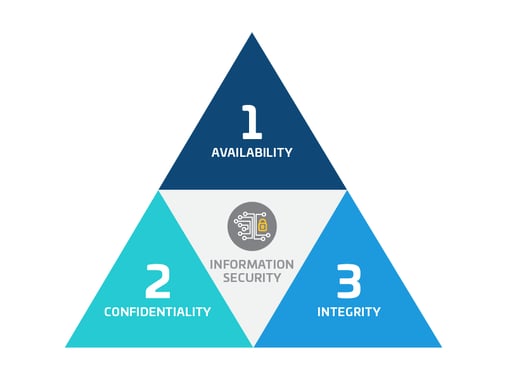
Security and compliance are built into Vesta’s processes and culture. We have been early adopters of compliance frameworks as well as the associated technologies. The security landscape is ever-changing and we strive to stay ahead of the curve and exceed requirements.
Compliance
Unlike other companies in the payments and fraud space, Vesta has been compliant for over a decade attested by third-party assessors and auditors. These controls are validated internally on a cyclical basis as well as by third-party assessors and auditors.
PCI 3.2.1 DSS Level 1 – Merchant and Service Provider
Vesta was an early adopter of PCI DSS dating back to 2004 when the first PCI DSS was released, and we have been PCI DSS Level 1 compliant since 2006. PCI DSS Level 1 is important to Vesta as it is attested to by a third-party PCI QSA (Qualified Security Assessor). Having third-party attestation gives guarantees that we are following controls and not self-assessing. Vesta also attests as both a Level 1 Merchant and Service Provider which is unique in the industry.
PCI 3-D Secure (PCI 3DS) Type 2 Level 1
Vesta is also PCI 3-D Secure (PCI 3DS) Type 2 attested by a third-party QSA which is a newer standard within PCI. We chose to be early adopters of this standard to further confidence with our partners, customers, and acquirers. PCI 3DS offers additional protections to reduce fraud and facilitate additional security for Card Not Present (CNP) transactions.
SSAE 18 SOC 1 Type 2 (Formally SAS 70/ SSAE 16)
Vesta has been SOC compliant since 2005. We only use AICPA certified third-party auditors assuring you that we are meeting our compliance controls. Our annual report is available to all our partners.
GDPR
Vesta has been GDPR compliance since 2018 as a Data Controller.
Security
Vesta’s Information Security Program is based on proven industry standard frameworks. These frameworks include PCI, SSAE 18, CIS, NIST 800 series of controls, ISO 2700x, and others. While we may not formally audit against all these standards, we closely follow industry best practices across these frameworks and incorporate the critical control aspects to provide a holistic approach to Information Security.
Dedicated Security and Compliance Team with 24/7 Monitoring
Vesta fields a security and compliance team with decades of experience and industry certifications such as SANS GIAC, (ISC)2, ISACA, and others. One of the most important aspects of the team is to continually research and expand our knowledge to combat the ever-changing threat landscape keeping our partners and customer data secure. We also strongly believe in cross-training all team members to minimize silos of knowledge. Vesta also monitors all our environments with a 24/7 Network Operations Center which coordinates with our Security and Compliance Team.
Frequent Cyclical Due-Diligence
Many companies do the minimum required to pass their compliance assessments and audits. At Vesta, we believe this is not enough and have adopted a monthly cyclical process that covers all our environments for a variety of controls. These controls far exceed requirements both from a technical and frequency standpoint.
- All Vesta external surfaces are scanned by a PCI ASV (Approved Scanning Vendor) monthly
- All Vesta environments have discovery scans monthly
- Vulnerabilities are reviewed, risk assessed and prioritized monthly
- Vesta utilizes live vulnerability monitoring which reports to our console multiple times a day
- Patches and vulnerability remediation are executed throughout the monthly cycle on a weekly basis
- User accounts are analyzed monthly
- Network penetration and segmentation testing are conducted by two different third-party security consulting companies on a bi-annual basis
- Many other frequent cyclical controls
Secure Data Communication, Privacy and Encryption
It is critical to Vesta that we protect your data, your customer's data and our own. For over a decade Vesta has utilized enterprise encryption technologies exceeding compliance requirements. Vesta strongly implements principles of least privilege and non-repudiation following industry best practices.
For data at rest, Vesta only implements FIPS 140-2 enterprise encryption technologies to protect data. We currently utilize multiple technologies for both HSM and Disk Encryption enforcing AES-256 cipher strength following NIST and PCI best-in-class recommendations. All Vesta endpoints implement PCI-compliant TLS 1.2 with no weak ciphers. These endpoints are also scanned monthly by a PCI ASV (Approved Scanning Vendor).
Over the Top Security, Research, and Feedback
At Vesta, we are constantly striving to be best-in-class with regard to security, compliance, and privacy. While we cannot discuss all our technologies and processes, be assured that we are doing our due diligence to be secure and are constantly researching to stay ahead of the curve. We also value our partner’s feedback and frequently incorporate ideas and technologies they suggest. Security and compliance are a company-wide effort and not just a “check the box” exercise.
.png)
.png)
%20(1).png)